Our daily lives are powered by mountains of code that underpin digital civilization. To secure these heaps of endpoints and digital infrastructure, bug bounty programs have emerged as an effective and ethical way to engage with hackers to counterbalance aggressive threat actors. However, historically, there has been some reluctance from program owners to reward participating hackers at market rates, mostly due to an outdated understanding of ROI.
At Bugcrowd, we strongly believe that:
- Appropriately rewarding hackers (see our rewards recommendations below) is an absolute requirement for all-around success in bug bounty, and
- The economic benefits of fair, market-rate payouts far outweigh their cost.
Let me explain why.
Case Study: MOVEit Transfer Vuln
The infamous MOVEit Transfer Critical Vulnerability (CVE-2023-35708) is a good example of how a relatively modest bug bounty reward would have paid for itself many, many times over.
As the Russian-speaking cyber syndicate Clop orchestrated a wave of extortion against numerous companies last season, the narrative was dominated by the scope of the incursion: numerous compromised organizations, personal data of millions siphoned, and copious volumes of sensitive information leaking into the dark web.
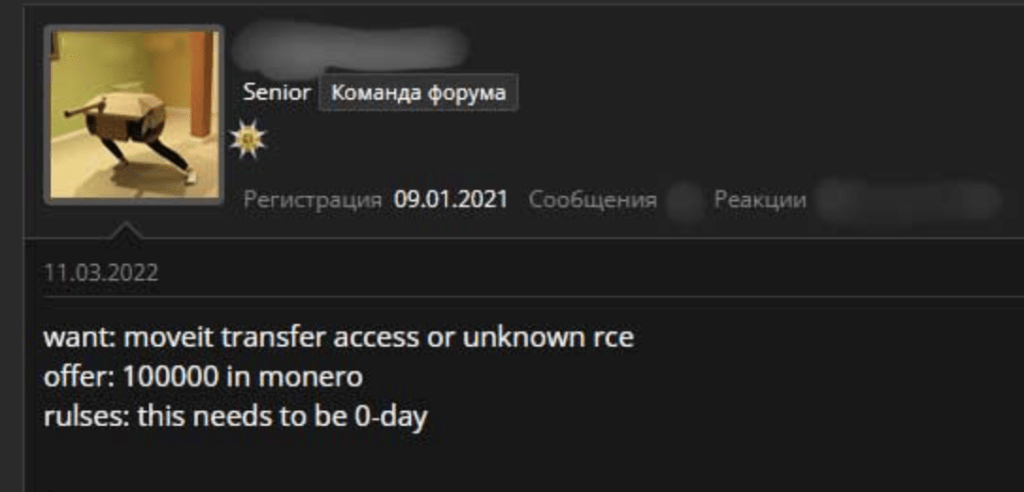
Central to this attack was the deployment of a zero-day exploit. Whether this vulnerability was a product of Clop’s own cyber reconnaissance – or, what seems more probable, procured from a dark web forum – it provided a digital crowbar to pry open defenses. Sifting through dark net forum posts reveals indicators that threat actors were actively paying large amounts of money for high-impact vulnerabilities:
Now let’s take a look into the known impact of the MOVEit Transfer vuln on organizations and individuals, to date:
Impacted organizations: 2,561
Impacted individuals: 67,174,909
In cybersecurity economics, quantifying the financial fallout of security incidents is napkin math. But it is very feasible to sketch an illustrative financial portrait by drawing from statistics reported in IBM’s Cost of a Data Breach Report 2023. If we apply the average toll of a data breach for each compromised record (US$165) to the tally of confirmed individuals affected by the incident, the estimated financial impact is a staggering US$11.08 billion. That figure speaks for itself!
Thinking ahead
When we speak with CISOs, it is common to hear the concern that implementing a robust bug bounty program will require a financial investment that can strain limited budgets. However, short-term thinking often leads to long-term problems.
For the sake of argument, let’s assume that a program commits to paying on the higher end of our suggested reward ranges with a payout of US$20,000, not US$5,000, for each critical vulnerability (and this assumes only one is found). The long-term impact would include:
- Long-term cost savings: Investing in a comprehensive bug bounty program can lead to substantial long-term cost savings because the cost of addressing a security breach far exceeds the cost of a $20,000 bounty payout: Per the Cost of a Data Breach Report 2023, the average total cost of a data breach is well over $4 million.
- Protection of brand reputation: The impact of a cyber attack on a company’s reputation can be devastating and long-lasting. Customers lose trust in brands that fail to protect their data, leading to churn and lost revenue. Customer trust is an invaluable asset that, once lost, is costly to regain–far more costly than $20,000.
- Competitive advantage: A strong security posture can be a competitive differentiator. Companies that demonstrate a commitment to security attract more customers and partnerships. A well-funded bug bounty program signals to the market that a company is serious about security, potentially giving it an edge over competitors. You could never buy that reputation with a paltry $20,000 marketing campaign.
- Avoidance of potential fines, legal fees, and insurance premiums: As we described in a previous post, a significant breach can lead to millions in downstream costs–making that $20,000 look like a really good investment.
- Access to expertise on-demand: Bug bounty programs on the Bugcrowd Platform crowdsource the expertise of the global security community, offering access to a diverse range of skills and perspectives that internal teams may lack. This access to a broader knowledge pool can augment, extend, and enhance a company’s security team far more effectively than relying solely on internal resources. Without it, do you have the ability or the funds to employ experts for every skill and asset 365 days a year?
Hackers agree: Per Bugcrowd’s 2023 Inside the Mind of a Hacker report, 84% of them believe that most organizations do not understand the true risks of a breach.
New recommended reward ranges
For the reasons above, there is no downside to scaling your program toward even the upper range of market-rate payouts over time. (Also keep in mind that your program is competing with others for hacker attention, and money talks.) In support of that point and to reflect the current marketplace, we recently updated our recommended reward ranges for bounty programs – informed by benchmarking the most successful programs on our platform after mapping hundreds of thousands of data points about vulnerability types, severity levels, and payouts:
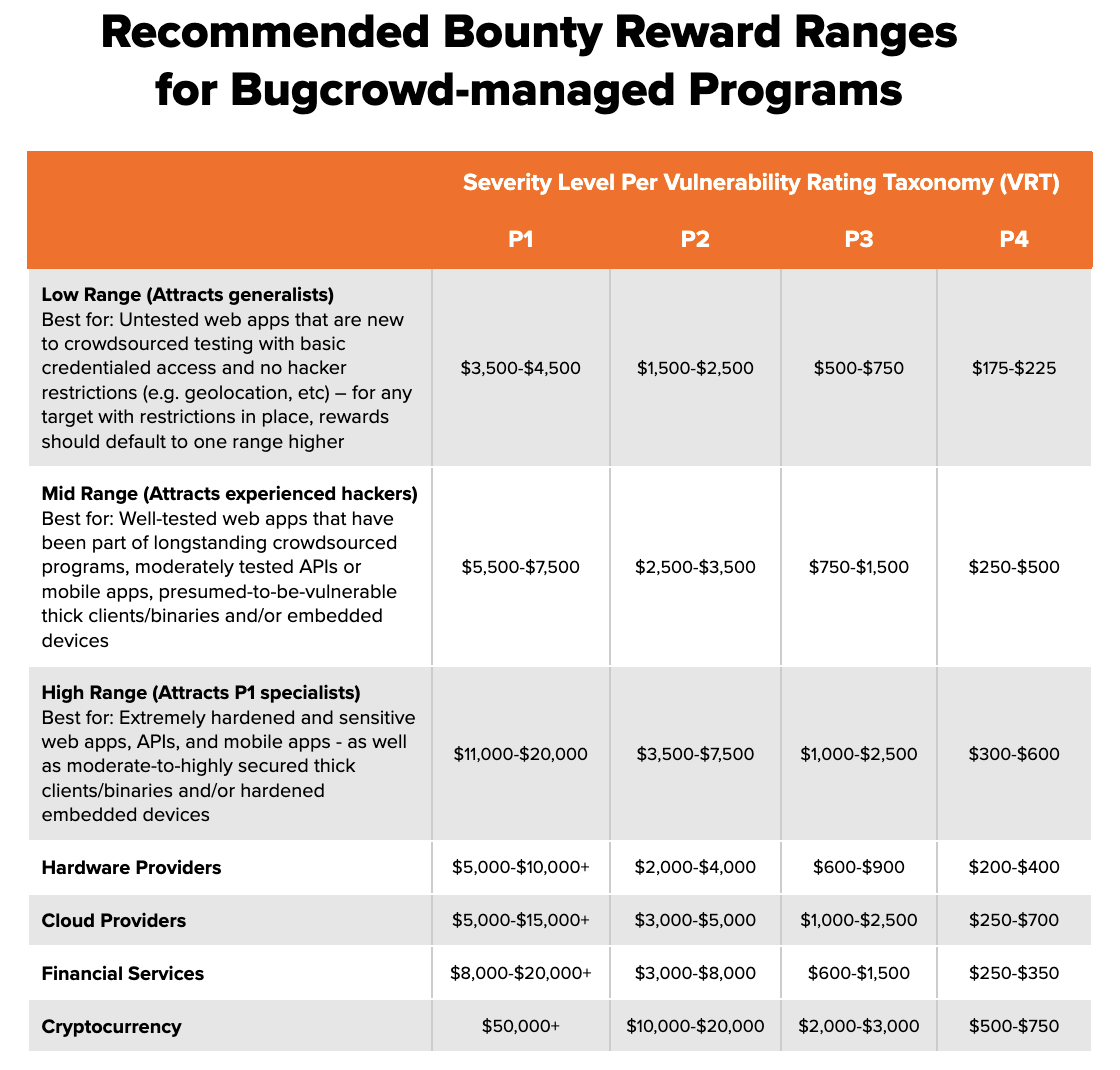
Respecting these recommendations is not only a proven method for enhancing impact, but it’s also the right thing to do for hackers who invest a lot of time in uncovering weaknesses that you want to hear about before potential threat actors do.
As market rates adjust over time, we continue to gather data about what makes successful programs work, and new categories (such as AI) emerge, we’ll make adjustments to these recommendations, as well.